Firstly, let's examine the contents of the
~/.ssh directory (~ being the linux shortcut for your home directory i.e. /home/{user}). Generally this directory only contains one file : known_hosts. What does this file contain? Well, every time you attempt to gain access to a user@host using ssh for the first time, you will be prompted with a message similar to this: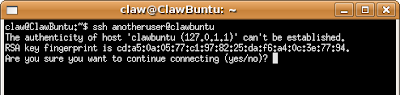
This is a built in security feature in ssh which will prevent other hosts from gaining illegal access by posing as someone else or spoofing. This file will contain a line representing each
user@host combination to have previously accessed your system using ssh.The files used for pre-authorized logins are not created by default. We're going to create them step-by-step now.
- Create a public / private key pair.
There are various types of keys available, for this example however, we're going to be using aRSAkey pair. We'll be making use of thessh-keygenutility to generate our key pair. - Place your public key on the remote system.
The second new file we're going to be dealing with is the~/.ssh/authorized_keysfile. The difference however, is that this file does not reside in your~/.sshdirectory, but in the~/.sshdirectory of the remote host. This file contains a line containing the public key of eachuser@hostcombination pre-authorized to log gain access to said system. i.e.user@hostcombinations who are not required to provide a password to gain access to the remote system.
Step 2 involves you placing the contents of your~/.ssh/id_rsa.pubfile in the remote system's~/.ssh/authorized_keysfile. Once you have done this, you will be pre-authorized to log into the remote system and will not be prompted to provide a password every time you log in.
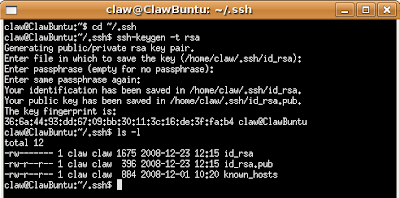
note: Just press enter to accept the defaults when prompted. Do Not Enter A Passphrase. You should now notice that your
~/.ssh directory contains two more files in addition to your known_hosts file; namely id_rsa and id_rsa.pub. As you may have suspected from the name id_rsa.pub is your public key file. This is the file we're going to be using for this exercise.note:
id_rsa is your private key file. Never give this file to anyone.- Use Copy & Paste between two terminals
- Use
scpto copy your~/.ssh/id_rsa.pubacross to the remote machine, and then append it manually
~/.ssh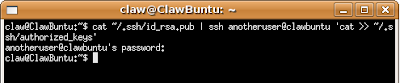
cat ~/.ssh/id_rsa.pub | ssh {user}@{host} 'cat >> ~/.ssh/authorized_keys'This will be the last time you ever need to enter the password again.


This is just what I need right now. A very good tip. Thank you for this.
ReplyDelete